Javascript Constable
Detect Data Skimming in Your Production Store
Non-Stop “Network Diff” of Your Live Site
- Non-stop crawling of your production site
- Performs complex synthetic transactions, such as login, product ordering, and more
- Logs all network activity, including first and third-party Javascript, images, CSS, XHR, and more
- Scours for new network activity
- Sends email alerts when suspicious network activity is detected, such as third-party XHR
- Uses domain whitelists and other configurations to eliminate false-positives (e.g., loading a new script from your domain)
Protect Against Magecart
Magecart is a nefarious group dedicated to eCommerce fraud. They’re unlike everyday hackers (they hold daily stand-ups, for instance): they’re skilled at finding new avenues to invade and poach customer data. Fluxguard detects and thwarts Magecart attacks.
Fluxguard monitors all network activity in your production CMS or Magento deployment. We detect and warn about suspicious, new XHR or third-party scripts loaded from unauthorized sites.
How to Activate Javascript Constable
1.Add the page/site and do an initial crawl
An initial crawl will collect a baseline of all data about the page, including a screenshot, complete HTML, extracted text, and a HAR network profile. After the initial crawl, examine the version network activity to review what was captured. (Download the HAR file for deeper analysis.)
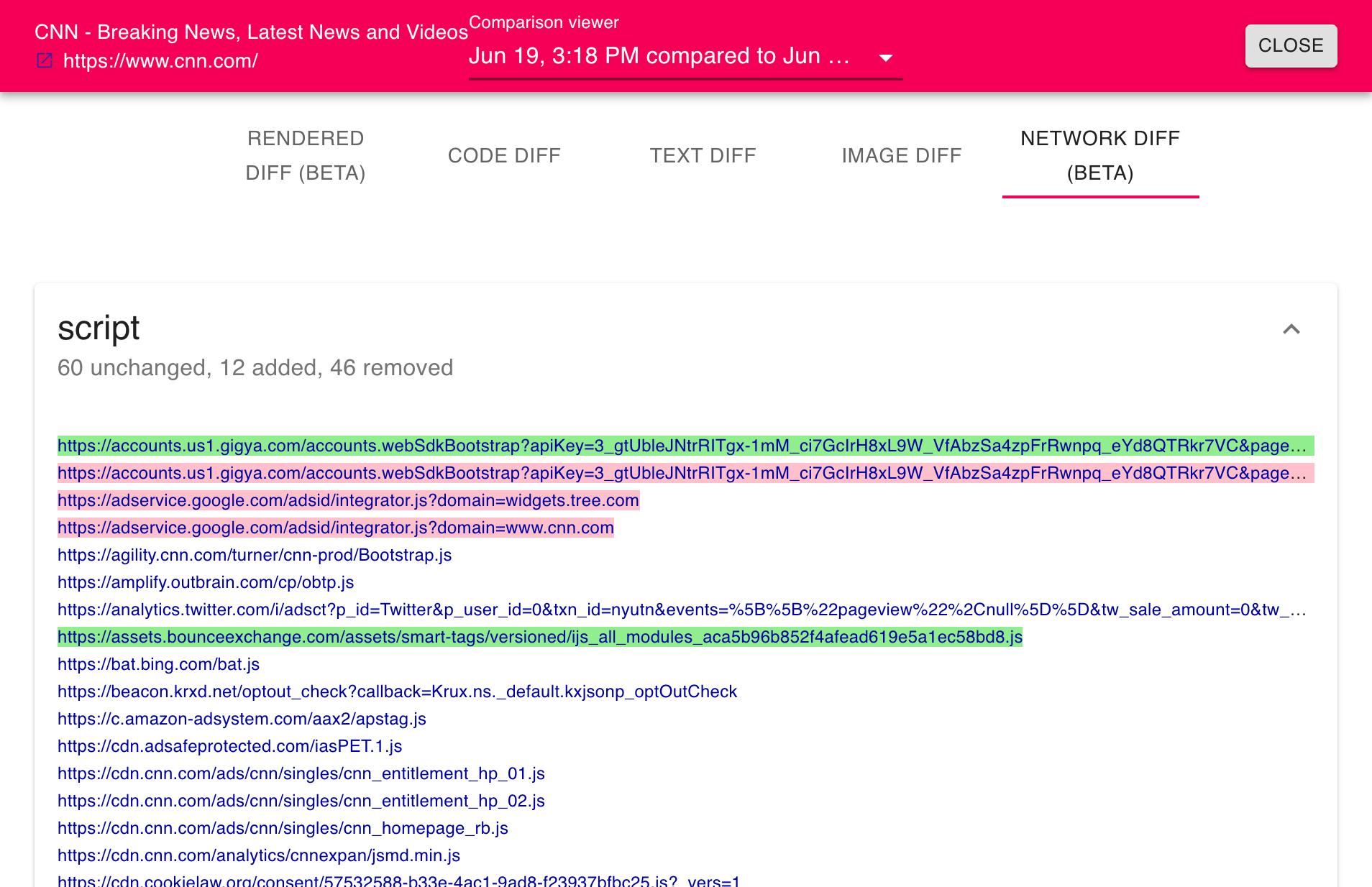
Notice all network activity is recorded by type (e.g., font, image, XHR, and so on). This data identifies network changes from one crawl to the next.
2.Click into Session Settings

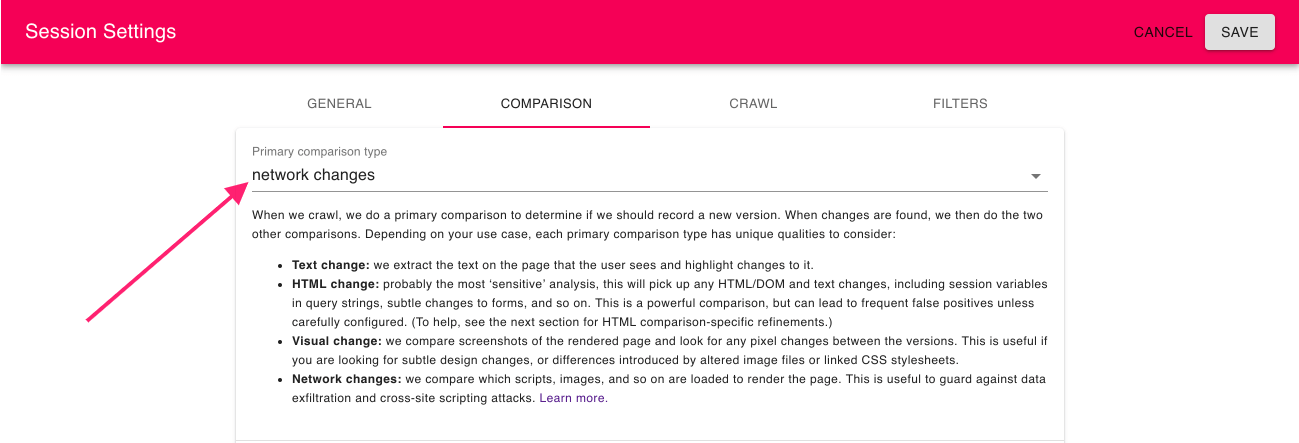
3.Click on the “Comparison” tab; modify the primary comparison to “network change”
For simplicity, Fluxguard uses a primary change detection strategy to establish if a new version should be registered. Replace the default “text change” to “network change.”
This will trigger a new version whenever a resource is added or removed. (Note: once a new version is registered, all comparisons will be conducted, including visual, text, and HTML.)
4.Observe and configure network-specific settings as an option
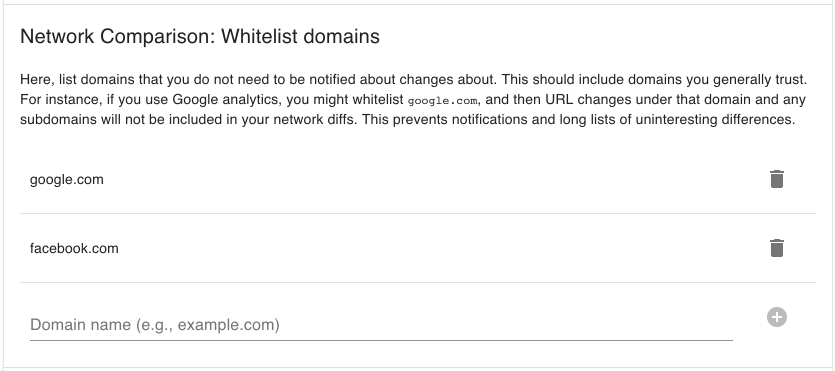
Reduce False-Positives by Whitelisting Domains
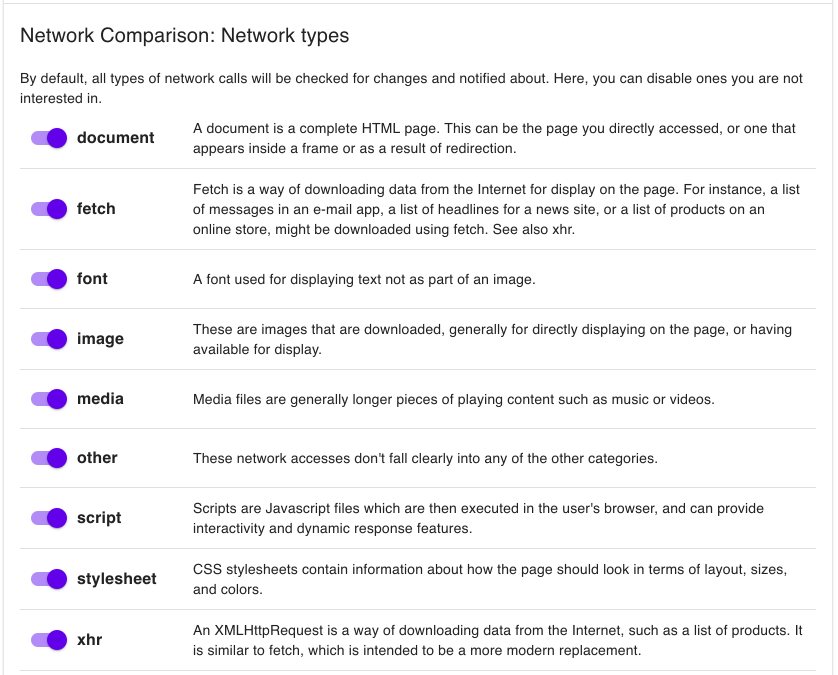
Refine Monitoring by Selecting Specific Resource Types
Data exfiltration can ensue place via the loading of almost any resource. Albeit certain network activities, such as scripts and XHR, are more susceptible. These settings allow you to activate various resource types. When a particular resource type is deactivated, a change in network requests for that group will not trigger new versions.
Opt for “Origins Only”
Use this setting if different URLs can be accessed from the same site, but you want to learn if a new site is utilized to fetch content. An example is to detect the injection of malicious Javascript that sends data off-site.
5.Adjust email alert frequency
Do you prefer to receive instant email alerts when network changes are detected? (The account default is to send a summary email every day.) If so, then go to Account Settings.
Once there, choose to receive alerts “immediately.” Afterward, you will receive an email itemizing all network changes in an instant.
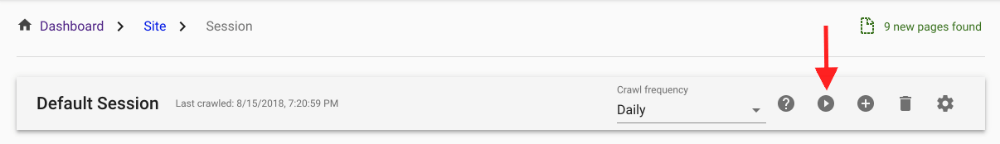
6.Wait for a network change
If you prefer, you can initiate a new crawl from Session View.