XSS & Data Exfiltration Prevention, XSS Attack, Javascript Injection
Non-Stop “Network Diff” of Your Live Site
Fluxguard provides deep network change monitoring and alerts. Execute synthetic transactions on your live site to identify data exfiltration and other skimming techniques. Our product offers:
- Non-stop crawling of your production site
- Performs complex synthetic transactions, such as login, product ordering, and more
- Logs all network activity, including first and third-party Javascript, images, CSS, XHR, and more
- Scours for new network activity
- Sends email alerts when suspicious network activity is detected, such as third-party XHR
- Uses domain whitelists and other configurations to eliminate false-positives (e.g., loading a new script from your domain)
Fluxguard provides a near real-time analysis of your network activity. In today’s eCommerce environment, this sort of audit becomes more necessary. Magecart and other thieves are invading eCommerce sites and stealing vital customer data.
In brief, Fluxguard’s general-purpose network and change monitoring detect “zero-day” attacks.
Protect Against Magecart
Magecart is a nefarious group dedicated to eCommerce fraud. They’re unlike everyday hackers (they hold daily stand-ups, for instance): they’re skilled at finding new avenues to invade and poach customer data. Fluxguard detects and thwarts Magecart attacks.
Javascript Injection & XSS Attack Detection
Fluxguard monitors all network activity in your production CMS or Magento deployment. We detect and warn about suspicious, new XHR or third-party scripts loaded from unauthorized sites.
How to Enable Network Difference Monitoring
1.Add the page/site and do an initial crawl
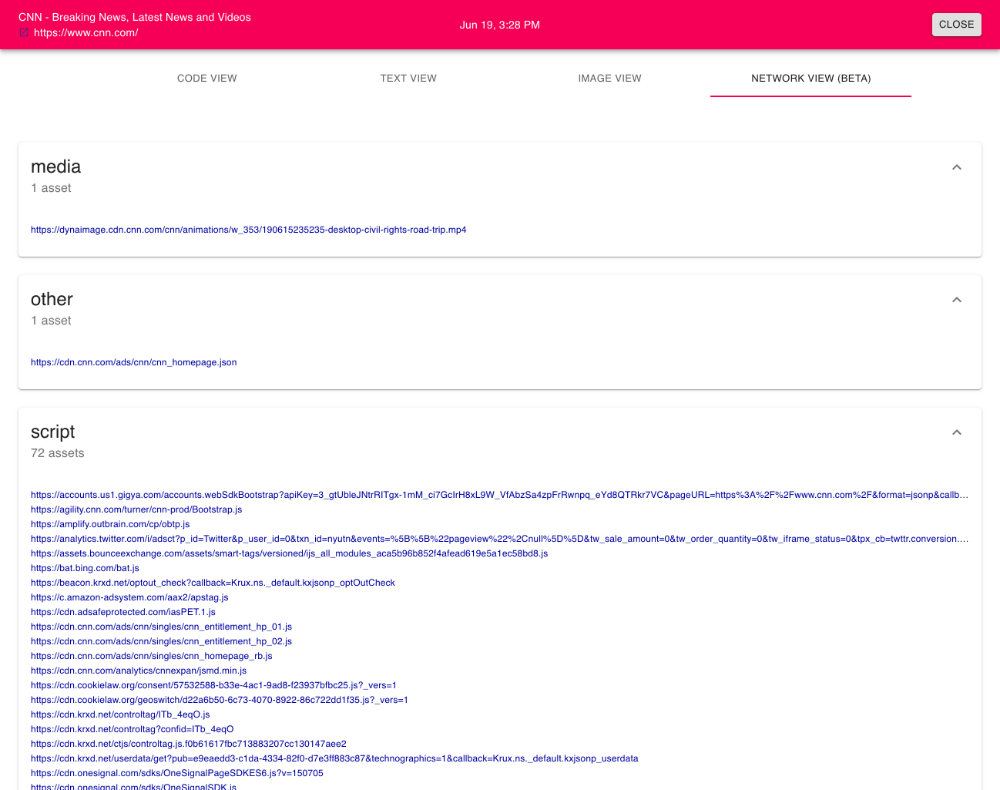
An initial crawl will collect a baseline of all data about the page, including a screenshot, complete HTML, extracted text, and a HAR network profile. After the initial crawl, examine the version network activity to review what was captured. (Download the HAR file for deeper analysis.)
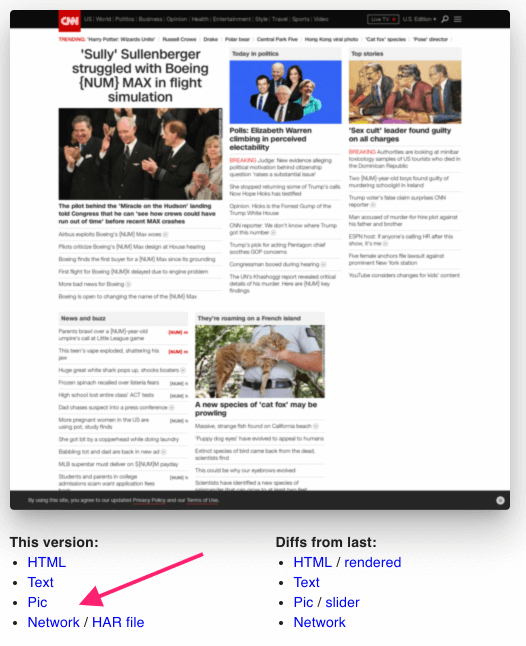
Notice all network activity is recorded by type (e.g., font, image, XHR, and so on). This data identifies network changes from one crawl to the next.
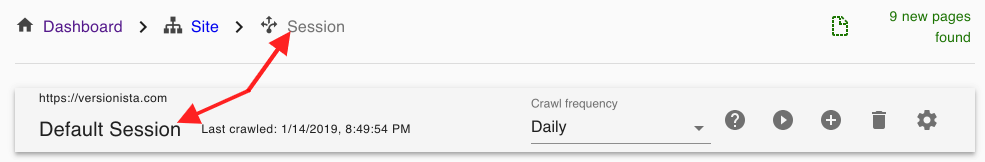
2.Click into Session Settings
Fluxguard allows you to add multiple sessions per site. A session can be considered a discrete user flow through a site: such as registering a user, ordering a product, and so on.
It’s at the session level where most of Fluxguard’s powerful configuration options are offered.
3.Click on the “Comparison” tab; modify the primary comparison to “network change”
For simplicity, Fluxguard uses a primary change detection strategy to establish if a new version should be registered. Replace the default “text change” to “network change.”
This will trigger a new version whenever a resource is added or removed. (Note: once a new version is registered, all comparisons will be conducted, including visual, text, and HTML.)
4.Observe and configure network-specific settings as an option
Once you select network change as your change detection strategy, new configuration possibilities are available. Most of these are designed to reduce false-positives. What’s a false-positive? A legitimate change... but an insignificant one. These can be intricate for network differences.
Let’s take a look.
Reduce False-Positives by Whitelisting Domains
You can whitelist certain domains. For instance, google.com, facebook.com, and even your domain may be somewhat tamper-resistant. As such, you can choose to add these and others.
Once accomplished, network additions or deletions from these domains will not trigger new versions. (However, to the extent other network events prompt a new version, all changes are displayed when viewing the network diff on Fluxguard.com.)
Refine Monitoring by Selecting Specific Resource Types
Data exfiltration can ensue place via the loading of almost any resource. Albeit certain network activities, such as scripts and XHR, are more susceptible. These settings allow you to activate various resource types. When a particular resource type is deactivated, a change in network requests for that group will not trigger new versions.
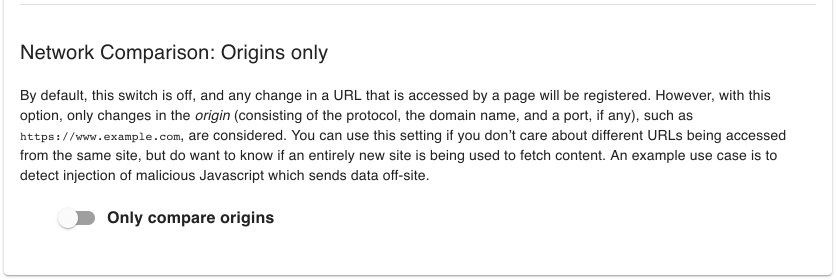
Opt for “Origins Only”
Use this setting if different URLs can be accessed from the same site, but you want to learn if a new site is utilized to fetch content. An example is to detect the injection of malicious Javascript that sends data off-site.
5.Adjust email alert frequency
Do you prefer to receive instant email alerts when network changes are detected? (The account default is to send a summary email every day.) If so, then go to Account Settings.
Once there, choose to receive alerts “immediately.” Afterward, you will receive an email itemizing all network changes in an instant.
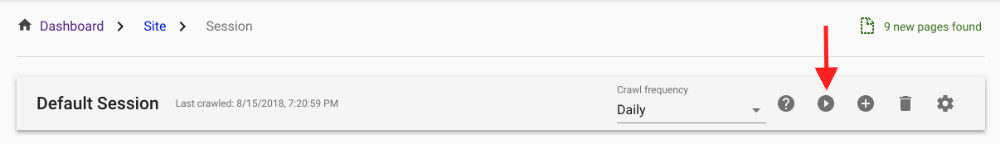
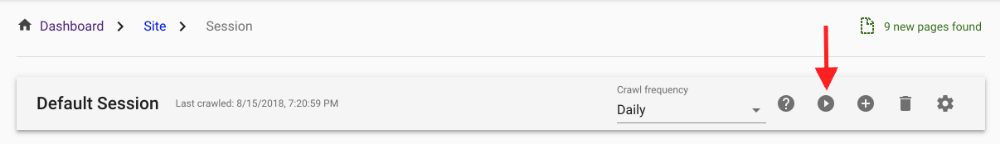
6.Wait for a network change
If you prefer, you can initiate a new crawl from Session View.
Depending on the network activity, this may result in a new version and an alert. Why? Some third-party scripts (from, e.g., Google) will always result in new network activity. It is best to reduce these false-positives (see step 4 above), yet, in this case any new version can be selected to take a look at the comparison output.
Once a new version is recorded, you will receive an alert (depending on the email frequency setting). Also, it is possible to use the comparison links below the thumbnail.
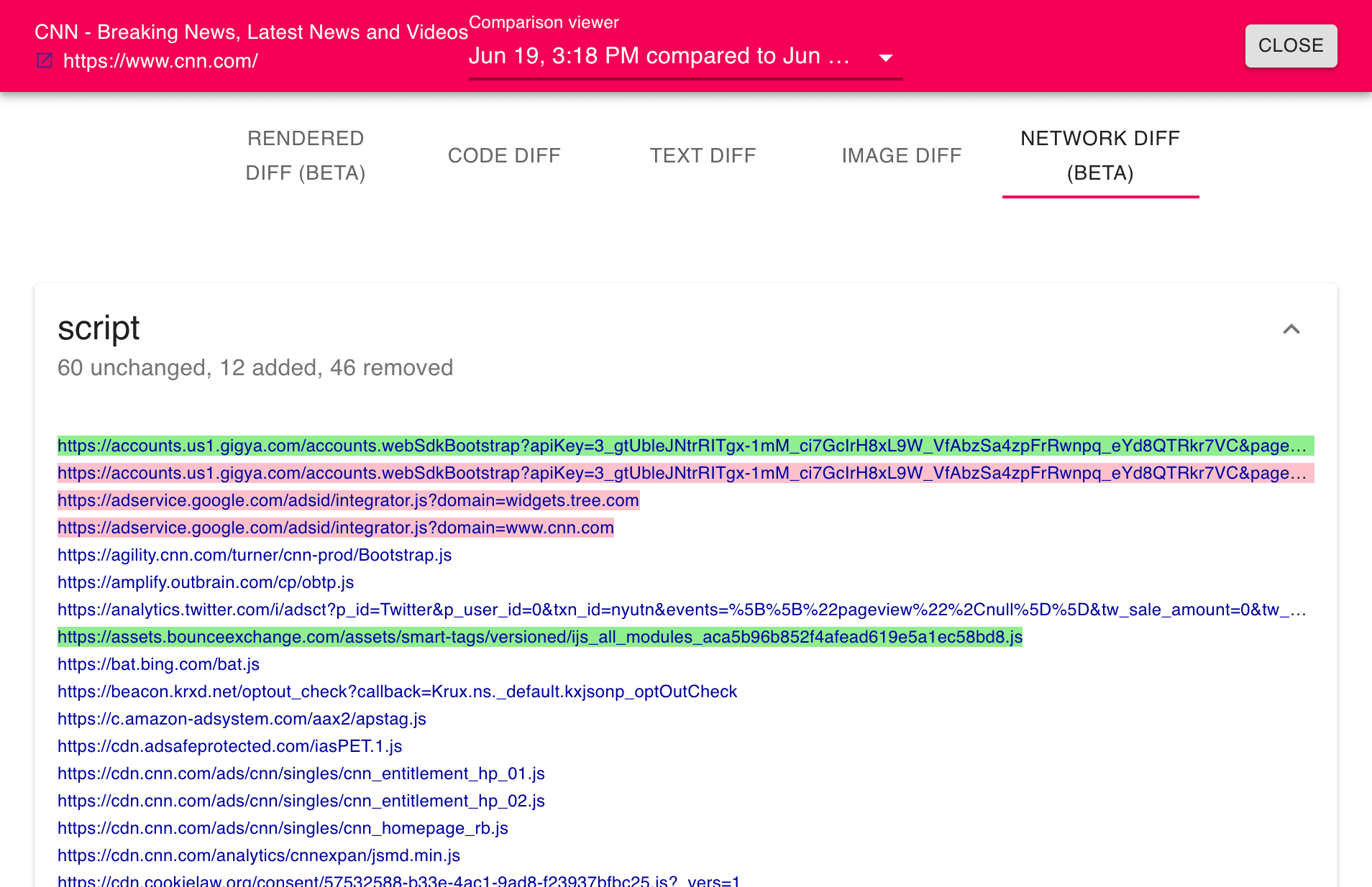
When the network comparison view is opened, you will find a list of network activity, grouped by type (e.g., XHR, image, font, and so on). Network activity changes are red (for a resource that is no longer loaded in the latest version) and green (for a resource that is new in the latest version).
Once the first network comparison completes, we suggest scrutinizing change activity. This is a great time to winnow false-positives from future alerts by using the configurations specified in the previous steps.
Data Exfiltration Detection and Javascript Threat Monitoring
Data Skimming Is a Critical Threat
Web security risks are growing, in particular for sites that transact vital customer data. Magecart, and other criminal hacking groups, often target eCommerce content management systems (CMS), such as Magento, and their ecosystems with sophisticated data skimming techniques.
Indeed, the threats from Magecart and others are genuine. These aren’t “just for the amusement” teenagers. Instead, these groups operate like modern software companies. They have stand-ups, OKRs, deliverables, and probably debate “agile,” too. But the purpose of all of this activity is to pilfter credit card and other personally-identifiable information (PII) from eCommerce sites.
At the core, the threat vectors for data exfiltration are endless: cross-site scripting, poisoned NPM modules, DNS spoofing and cache poisoning, infected third-party plugins, compromised vendors, disgruntled ex-employees, and on and on. And detection is often a cat-and-mouse game, with attackers often disguising and obscuring exfiltration.
We Provide Non-Stop “Network Diff” Alerts
Fluxguard offers a unique solution. We monitor network activity across customers’ key user journeys, such as account registration and product ordering. We report suspicious, unknown XHR, script, and other network activity for investigation and remediation.
Fluxguard alerts you to network changes by non-stop, automated monitoring of your production site. For instance, our software will crawl and submit forms on key pages, such as:
- Go to the home page
- Login
- Add a product
- Checkout
- And so on
And while Fluxguard monitors changes to the underlying HTML, our new network diff feature tracks network changes, such as new scripts, XHR, fonts, images, and so on. And we do so for every monitored page.
We also provide various configuration options, including domain whitelists, to reduce false-positives. This way, you’re only alerted to dubious network changes.
How to Get Started
Enabling network diff’ing is simple. Here’s how:
1. Add the page/site and do an initial crawl
An initial crawl will collect a baseline of all data about the page, including a screenshot, complete HTML, extracted text, and a HAR network profile. After the initial crawl, examine the version network activity to review what was captured. (Download the HAR file for deeper analysis.)

Notice all network activity is recorded by type (e.g., font, image, XHR, and so on). This data identifies network changes from one crawl to the next.
2.Click into Session Settings
Fluxguard allows you to add multiple sessions per site. A session can be considered a discrete user flow through a site: such as registering a user, ordering a product, and so on.
It’s at the session level where most of Fluxguard’s powerful configuration options are offered.
3.Click on the “Comparison” tab; modify the primary comparison to “network change”
For simplicity, Fluxguard uses a primary change detection strategy to establish if a new version should be registered. Replace the default “text change” to “network change.”
This will trigger a new version whenever a resource is added or removed. (Note: once a new version is registered, all comparisons will be conducted, including visual, text, and HTML.)
4.Observe and configure network-specific settings as an option
Once you select network change as your change detection strategy, new configuration possibilities are available. Most of these are designed to reduce false-positives. What’s a false-positive? A legitimate change... but an insignificant one. These can be intricate for network differences.
Let’s take a look.
Reduce False-Positives by Whitelisting Domains
You can whitelist certain domains. For instance, google.com, facebook.com, and even your domain may be somewhat tamper-resistant. As such, you can choose to add these and others.
Once accomplished, network additions or deletions from these domains will not trigger new versions. (However, to the extent other network events prompt a new version, all changes are displayed when viewing the network diff on Fluxguard.com.)
Refine Monitoring by Selecting Specific Resource Types
Data exfiltration can ensue place via the loading of almost any resource. Albeit certain network activities, such as scripts and XHR, are more susceptible. These settings allow you to activate various resource types. When a particular resource type is deactivated, a change in network requests for that group will not trigger new versions.
Opt for “Origins Only”
Use this setting if different URLs can be accessed from the same site, but you want to learn if a new site is utilized to fetch content. An example is to detect the injection of malicious Javascript that sends data off-site.
5.Adjust email alert frequency
Do you prefer to receive instant email alerts when network changes are detected? (The account default is to send a summary email every day.) If so, then go to Account Settings.
Once there, choose to receive alerts “immediately.” Afterward, you will receive an email itemizing all network changes in an instant.
6.Wait for a network change
If you prefer, you can initiate a new crawl from Session View.
Depending on the network activity, this may result in a new version and an alert. Why? Some third-party scripts (from, e.g., Google) will always result in new network activity. It is best to reduce these false-positives (see step 4 above), yet, in this case any new version can be selected to take a look at the comparison output.
Once a new version is recorded, you will receive an alert (depending on the email frequency setting). Also, it is possible to use the comparison links below the thumbnail.
When the network comparison view is opened, you will find a list of network activity, grouped by type (e.g., XHR, image, font, and so on). Network activity changes are red (for a resource that is no longer loaded in the latest version) and green (for a resource that is new in the latest version).
Once the first network comparison completes, we suggest scrutinizing change activity. This is a great time to winnow false-positives from future alerts by using the configurations specified in the previous steps.